Comunicação com comprovativo de envio e receção
Notificação eletrónica
Na Lleida.net paga apenas pelo que consome. Não cobramos pelo registo ou subscrição, e as compras nunca expiram
Tão fácil como enviá-los por e-mail
Assine documentos e contratos
Possuímos interligações com operadoras em mais de 150 países.
Soluções SMS e voz IP
As nossas sedes Presença internacional
Lleida
Madrid
Paris
London
Miami
Dubai
San José
Bogotá
São Paulo
Tokyo
Santo Domingo
Cape Town
Johannesburg
Montevideo
Santiago de Chile
Lima
Beirut
Ciudad de México
Clientes satisfeitos com os nossos serviços
Histórias de sucesso
We particularly loved the ease and agility of contracting the system and its credit-based use. In other words, you top up some credits and start working without too much training, without any specific software installation or technical complexity
Registered notification service has made possible to help in the internal operating processes of companies and in their digital transformation.
A Lleida.net dá-nos tranquilidade e garante que os pais verificam a contratação do nosso serviço de forma simples e, acima de tudo, segura e legalmente válida.
O Connectaclick Pro permitiu-nos criar uma solução completamente personalizada e à medida para a HolaLuz, um must para qualquer serviço que pretendermos integrar nos nossos processos.
Este acordo tem em vista fornecer segurança, confiança e eficácia aos nossos utilizadores para oferecer uma comunicação e atenção de máxima qualidade










Notícias, tutoriais, entrevistas, etc.
O Blog

 19 Fevereiro, 2026
19 Fevereiro, 2026
Compliance with Spain energy regulation RD 88 2026 for electricity suppliers obligations penalties and how to prove customer consent.
Compliance with Spain energy regulation RD 88 2026 became mandatory on 12 February 2026.
For electricity suppliers operating in Spain this is not simply a regulatory update. It redefines how commercial relationships must be documented, how customer consent must be captured, and how every interaction must be proven under regulatory scrutiny
The objective of the regulation is clear. Increase transparency. Protect consumers. Modernise the electricity market in line with European energy transition goals.
The operational impact is equally clear.
Suppliers must now rethink communication processes, consent management and documentation systems. Every commercial action must be traceable and defensible.
The central question is no longer whether your organisation complies.It is whether you can prove it.
Without registered digital traceability, exposure to enforcement action is real.
Why Royal Decree 88/2026 matters for the Spanish energy sector
The regulation introduces immediate changes across core commercial operations.
Contractual communication
Suppliers must
- Notify contractual modifications at least 30 days in advance
- Send notifications separately from invoices
- Ensure communications are clear, accessible and transparent
Express consent
- Signed documents and all contracting evidence must be preserved throughout the entire lifecycle
- Full recordings of telephone contracting must be retained
- Signed documents and all contracting evidence must be preserved throughout the entire lifeycle
Supplier switching
Suppliers must
- Ensure full traceability of the switching process
- Respect maximum deadlines of 10 working days
- Complete technical execution within 24 hours
Customer service
Suppliers must provide
- Free customer service channels
- Electronic acknowledgements of receipt
- Documented responses, including formally recorded complaints
Data protection
The regulation reinforces
- Data protection security and confidentiality obligations
- Strict controls regarding access to the Supply Point Information System SIPS
In addition, unsolicited commercial calls to individuals are prohibited. Traditional outbound telesales models must be fundamentally reassessed.
Penalties for non-compliance: real risks for electricity suppliers
Non-compliance is supervised by the Ministry and the CNMC.
Sanctions may include
- Financial penalties of up to 6 million euros
- Formal consumer claims
- Temporary suspension of access to SIPS which may result in operational paralysis
- Reputational damage and loss of market confidence
The most significant risk, however, is evidentiary.
If a supplier cannot demonstrate that a notification was delivered that consent was explicitly granted or that switching deadlines were respected, regulatory exposure increases immediately. Every undocumented interaction becomes a vulnerability during inspection.
How to ensure compliance through registered digital traceability
Compliance under Spain energy regulation RD 88 2026 requires certainty. Electricity suppliers must be able to demonstrate every communication with legally valid evidence.
LLeida.net Registered digital solutions embed proof directly into operational workflows, allowing organisations to document consent, preserve evidence, and maintain full audit readiness without increasing friction.
Registered digital solutions for electricity suppliers
For legally valid contractual communications, including:
- Contract modifications with proof of receipt
- Price revisions with full traceability
- Suspension or reconnection notices
- Any mandatory regulatory communication requiring demonstrable evidence
For urgent notifications requiring proof of delivery and reading such as
- Suspension alerts
- Reconnection confirmations
- Supply change notifications
Electronic signature Click and Sign
Capture express consent with full legal validity across digital telephone or hybrid channels.
Each signature includes:
- Timestamp
- Identity linkage
- Complete process traceability
Electronic custody and traceability
Secure storage and immediate retrieval of evidence for CNMC audits and regulatory inspections. Documentation remains accessible whenever required.
Identity verification and document validation
For onboarding new contracts and sensitive processes:
- eKYC with liveness detection
- Identity document validation
- Enhanced authentication
- Digital certificate verification
- Security begins at the first interaction.
For suppliers managing high volumes or complex commercial flows, tailored automation ensures:
- Traceability at every step
- Reduced operational risk
- Consistent regulatory compliance
In 2026, registered digital evidence is no longer a best practice. It is a compliance requirement and a risk management necessity. Suppliers who adapt early will not only reduce. They will improve operational resilience and strengthen consumer trust.
Practical cases applying the regulation in everyday operations
The following scenarios illustrate how routine processes must evolve after February 2026
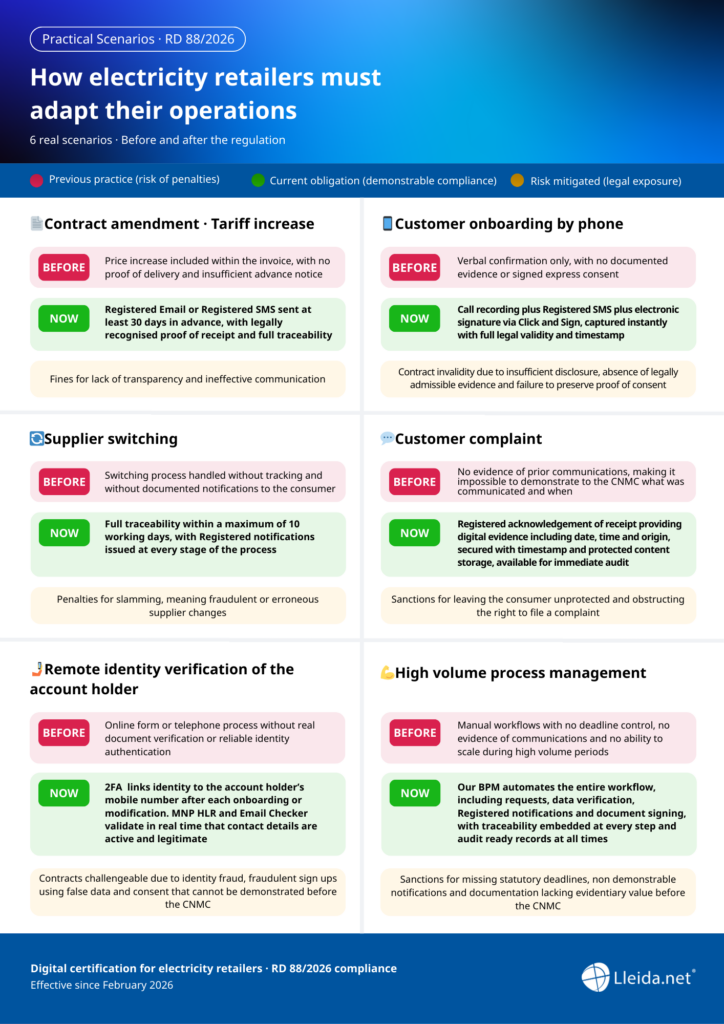
In each case, the common denominator is the same. Move from processes that cannot be demonstrated to registered digital evidence with full legal validity. Registered traceability is not a technical enhancement.It is the difference between compliance and the inability to defend it.
Take the step towards full compliance
Although the regulation requires adaptation, it also creates opportunity.
- More transparent processes
- Stronger consumer confidence
- Automation of critical workflows
- Reduced regulatory exposure
Electricity suppliers that implement registered digital traceability now will transform regulatory pressure into operational strength.
Is your organisation ready for 2026 compliance?

 16 Fevereiro, 2026
16 Fevereiro, 2026
Lleida.net recognised as a key technology partner in the 2025 ADECOSE Industry Report
The digital transformation of the insurance sector has reached a critical tipping point. What was once a strategic objective has now become a baseline operational reality. The 2025 ADECOSE Barometer, the definitive annual study for one of Europe’s most digitally mature insurance markets, highlights a significant milestone: over 90% of brokerages have now adopted a unified, standardised platform for data exchange and policy management
This structural shift goes beyond simple connectivity. It represents a move towards a fully integrated digital ecosystem where eSignatures and certified communications are native components of the workflow.
Within this high-standard environment, Lleida.net has once again been named a top-tier provider, serving as the technological backbone for firms that require absolute legal certainty under eIDAS regulations.
Beyond the Barometer: Why this is a global benchmark for Insurance
The ADECOSE Barometer, published by the leading association for insurance brokerages in Spain, is much more than a local satisfaction survey. It is a rigorous analysis of how top-tier insurers and tech partners handle the "trinity" of modern insurance: operational efficiency, customer experience, and strict regulatory compliance.
For international firms, the report serves as a roadmap. It tracks the successful implementation of standardised data protocols (such as EIAC) and the mass adoption of centralised platforms like CIMA.
By proving that 90.4% of a market can successfully migrate to a "Digital Policy" model, it sets a new standard for the global industry. Lleida.net’s prominent role in this report confirms our ability to deliver solutions that are not only innovative, but also legally robust enough to stand up in any court.
CIMA reaches 90% adoption: A benchmark for digital insurance
The 2025 ADECOSE Barometer confirms the absolute success of the CIMA platform. Currently 90.4% of brokerages use this system. This high adoption rate establishes CIMA as the industry standard. It marks a decisive milestone in the implementation of the Digital Policy project.
CIMA ensures interoperability through the EIAC standard. This protocol allows insurers and brokers to share data in a structured and efficient manner. The system provides a secure environment for all participants in the insurance distribution chain.
However, the platform offers much more than simple connectivity. CIMA integrates eSignature in insurance as a native service. This feature allows brokers to sign policies with full legal validity without leaving the platform.
Since 2023, brokers have utilised Click & Sign within their familiar operational workflows. This integration removes friction and significantly accelerates closing times. The result is a seamless experience for both the broker and the policyholder.
End-to-end security for the modern insurer
Lleida.net provides the comprehensive digital infrastructure that modern insurance requires. A simple signature is no longer enough to protect against sophisticated fraud; companies now need an auditable trail of evidence for the entire contract lifecycle.
Our suite of services includes registered communications with verified senders, providing a probatory record of every interaction.
Our Solution Capabilities
Registered Communications with Verified Senders, We ensure full traceability and evidentiary value for every policyholder interaction. This process creates a robust legal audit trail for your peace of mind.
Digital Identity Verification (eKYC and Digital ID) Our tools use remote video identification with proof of life or digital certificates. This technology significantly reduces identity fraud in the eSignature in insurance workflow.
Qualified Electronic Signatures We provide digital certificate signatures for high stakes legal operations. Our system fully complies with eIDAS regulations.
Registered Document Vaulting, We preserve the evidentiary value of every transaction. This service mitigates legal risks during critical processes such as claims or audits.
Our solutions build a digital trust ecosystem that meets every industry demand.
Lleida.net: The partner for top-rated insurers
A high percentage of the top-rated insurers in the ADECOSE Barometer already use Lleida.net. We help them transform their contracting processes with measurable success.
The results of our eSignature in insurance solutions speak for themselves:
✓ 80% reduction in turnaround time, moving from days to minutes.
✓ Zero physical archiving costs for direct savings on infrastructure.
✓ 100% regulatory compliance with zero legal risks.
✓ Enhanced customer experience and higher conversion rates.
Is your brokerage ready to compete with the new industry standard?

 9 Fevereiro, 2026
9 Fevereiro, 2026
eIDAS 2.0 for businesses: a practical guide to getting ready
eIDAS 2.0 for businesses is reshaping how organisations prove identity, sign documents and exchange information online. With the regulation now in force, Europe is taking a clear step towards simpler digital interactions, stronger legal certainty and a more coherent Digital Single Market across Member States.
This is more than a regulatory milestone. eIDAS 2.0 reflects a broader European shift: building a shared digital foundation based on trust, interoperability and a user-first approach to data and identity.
eIDAS 2.0 and the role of the European Digital Identity
Good technology should remove friction, not introduce it. That idea sits at the core of eIDAS 2.0 and its central element: the European Digital Identity Wallet (EUDI Wallet).
The EUDI Wallet will allow individuals and organisations to access a secure, verifiable, and free digital wallet from any device. Through it, users will be able to store and present trusted digital credentials, such as identity documents, academic qualifications, professional certificates or licences, and sign electronic documents with full legal validity across the European Union.
Digital identity is, therefore, becoming a basic building block of modern digital services. Combined with qualified trust services, it supports secure transactions, streamlines processes, and helps deliver digital experiences that feel simple, intuitive, and reliable, across both the public and private sectors.
Adapting to eIDAS 2.0 for businesses: a competitive edge before it becomes mandatory
For eIDAS 2.0 for businesses, this regulation signals a clear change in direction. Digital processes will no longer rely on fragmented national solutions but increasingly on a shared, pan-European infrastructure. Qualified trust services and verifiable credentials move from the margins to the centre of digital operations.
The EUDI Wallet will operate under common technical standards across all Member States. Importantly, the European Commission has confirmed compatibility with existing trust services, allowing organisations to evolve gradually rather than face abrupt change.
Getting ready early is not just about compliance. For businesses, it is a chance to modernise digital workflows, align systems with the European model and gain an advantage, while avoiding rushed, costly changes further down the line.
A roadmap for eIDAS 2.0 for businesses: where to begin
Review your current digital processes to spot gaps and opportunities
The starting point is clarity. How are digital identities currently used across your organisation? How do you onboard customers, employees, or suppliers? Where do electronic signatures or certified communications play a role? How is legally valid evidence stored and protected over time?
Mapping these processes now makes it easier to plan a structured transition, rather than responding under pressure once new requirements become unavoidable.
Identify the qualified trust services your business actually needs
The eIDAS framework defines a set of qualified identification and trust services that carry legal effect across the EU. These services form the technical backbone of the future European Digital Identity Wallet and are essential for operating confidently within the Digital Single Market.
That said, not every organisation needs every service. The focus should be on selecting what genuinely adds value to each process, while ensuring compliance. Consider whether you need:
- Qualified eIDAS electronic signatures for contracts or documents requiring the highest level of legal certainty.
- Qualified timestamping to prove when a document was created or modified, even years later.
- Qualified electronic seals and digital certificates to guarantee authorship, integrity, and a legally recognised organisational identity.
- Certified electronic communications (electronic registered delivery) where notifications must provide proof of sending, receipt and access.
- Universal Signed Document Verifier to validate third-party electronic signatures and certificates in real time.
- Lleida.net Wallet to keep a digital certificate on a mobile device and sign documents in a qualified, fast and secure way.
At Lleida.net, we deliver qualified trust services tailored to specific sectors and use cases, supported by complementary solutions for end-to-end digital transformation.
Choose interoperable, scalable, and certified solutions
Interoperability is a core principle of eIDAS 2.0 for businesses. To implement it successfully, organisations should:
- Avoid closed or purely local solutions that limit future compatibility.
- Rely on services aligned with European standards and supported by recognised security certifications such as ISO 27001, ISO 9001 and ENS High Level.
- Integrate services through REST APIs, making it easier to embed qualified trust services into existing systems and prepare for the wider eIDAS 2.0 ecosystem with both technical and legal assurance.
You can review all Lleida.net security and quality certifications required to ensure the highest level of trust.
Work with an experienced Qualified Trust Service Provider
The choice of partner matters. An experienced, Qualified Trust Service Provider can mean the difference between a smooth transition and an unnecessarily complex one.
- Certified infrastructure that meets demanding European standards
- In-depth regulatory knowledge of eIDAS, GDPR, ETSI and sector-specific frameworks
- Proven experience across multiple industries
- Long-term technical and legal support as requirements evolve
Lleida.net is a Qualified Trust Service Provider with more than 30 years of experience supporting organisations as they digitalise with full legal certainty. From initial assessment to full implementation, we help ensure your organisation is ready for eIDAS 2.0 from day one.
Ready to prepare your business for eIDAS 2.0?
Speak to our experts and see how regulatory readiness can become a genuine competitive advantage.

Frequently asked questions about eIDAS 2.0
What is eIDAS 2.0?
eIDAS 2.0 is the updated European regulation on digital identity and trust services, creating a single legal framework across the EU.This new version redefines key aspects of the framework.
- EUDI Wallet (European Digital Identity Wallet): a secure and free digital wallet for citizens and businesses
- Expanded qualified trust services with legal validity across all Member States
- Greater interoperability for cross-border digital interactions
- Stronger security requirements for qualified service providers
eIDAS 2.0 applies to both public and private sectors, including financial services, insurance, healthcare, telecommunications and e-commerce. As a Qualified Trust Service Provider, Lleida.net already offers solutions aligned with these requirements.
When does eIDAS 2.0 come into force?
eIDAS 2.0 entered into force on 20 May 2024, with a phased rollout:
- 2024–2025: publication of technical standards
- By the end of 2026: Member States must provide at least one EUDI Wallet
- From 2027 onwards: mandatory acceptance by regulated services and large private platforms
Organisations that prepare ahead of 2026 will reduce risk and gain a clear competitive edge.
Is eIDAS 2.0 mandatory for my business?
It depends on your sector and activities, but many organisations will face clear obligations.
Your business will need to comply with eIDAS 2.0 if you:
- Provide public or regulated services
- Operate large online platforms in the EU
- Work in financial or insurance sectors
- Provide regulated telecommunications services
- Manage processes that require legally recognised identification
In these scenarios, organisations must accept the European Digital Identity Wallet (EUDI Wallet) as a valid method of identification and authentication when a user presents it.
The full legal text is available on EUR-Lex, the European Union’s official legislation portal:
https://eur-lex.europa.eu/eli/reg/2024/1183/
What if you’re an SME or operate outside regulated sectors?
Even if eIDAS 2.0 isn’t mandatory for you, adopting it early can be a smart move. It helps simplify onboarding, build trust from the start, and position your business for future growth, turning early readiness into a competitive advantage.
